Update Functional Specification
This commit is contained in:
parent
db2a65fd3c
commit
49a79658aa
Binary file not shown.
@ -1,8 +1,73 @@
|
||||
# Functional Specification
|
||||
## 0. Table of Contents
|
||||
1. [Introduction](#1-Introduction)
|
||||
1. [Overview](#11-Overview)
|
||||
2. [Business Context](#12-Business-Context)
|
||||
3. [Glossary](#13-Glossary)
|
||||
1. [Panoptes](#131-Panoptes)
|
||||
2. [General Description](#2-General-Description)
|
||||
1. [Product/System Functions](#21-ProductSystem-Functions)
|
||||
2. [User Characteristics and Objectives](#22-User-Characteristics-and-Objectives)
|
||||
3. [Operational Scenarios](#23-Operational-Scenarios)
|
||||
1. [Module Installation](#231-Module-Installation)
|
||||
2. [Module Control](#232-Module-Control)
|
||||
3. [Function Permission Denied](#233-Function-Permission-Denied)
|
||||
4. [User Login and Verification](#234-User-Login-and-Verification)
|
||||
4. [Constraints](#24-Constraints)
|
||||
1. [Security Constraints](#241-Security-Constraints)
|
||||
2. [Server Constraints](#242-Server-Constraints)
|
||||
3. [Timing Constraints](#243-Timing-Constraints)
|
||||
3. [Functional Requirements](#3-Functional-Requirements)
|
||||
1. [User Authentication](#31-User-Authentication)
|
||||
1. [Description](#311-Description)
|
||||
2. [Criticality](#312-Criticality)
|
||||
3. [Technical Issues](#313-Technical-Issues)
|
||||
4. [Dependencies](#314-Dependencies)
|
||||
2. [Hierarchy Management](#32-Hierarchy-Management)
|
||||
1. [Description](#321-Description)
|
||||
2. [Criticality](#322-Criticality)
|
||||
3. [Technical Issues](#323-Technical-Issues)
|
||||
4. [Dependencies](#324-Dependencies)
|
||||
3. [Module Installation](#33-Module-Installation)
|
||||
1. [Description](#331-Description)
|
||||
2. [Criticality](#332-Criticality)
|
||||
3. [Technical Issues](#333-Technical-Issues)
|
||||
4. [Dependencies](#334-Dependencies)
|
||||
4. [Module Control](#34-Module-Control)
|
||||
1. [Description](#341-Description)
|
||||
2. [Criticality](#342-Criticality)
|
||||
3. [Technical Issues](#343-Technical-Issues)
|
||||
4. [Dependencies](#344-Dependencies)
|
||||
5. [Container Orchestration](#35-Container-Orchestration)
|
||||
1. [Description](#351-Description)
|
||||
2. [Criticality](#352-Criticality)
|
||||
3. [Technical Issues](#353-Technical-Issues)
|
||||
4. [Dependencies](#354-Dependencies)
|
||||
6. [Statistics Display](#36-Statistics-Display)
|
||||
1. [Description](#361-Description)
|
||||
2. [Criticality](#362-Criticality)
|
||||
3. [Technical Issues](#363-Technical-Issues)
|
||||
4. [Dependencies](#364-Dependencies)
|
||||
7. [Security](#37-Security)
|
||||
1. [Description](#371-Description)
|
||||
2. [Criticality](#372-Criticality)
|
||||
3. [Technical Issues](#373-Technical-Issues)
|
||||
4. [Dependencies](#374-Dependencies)
|
||||
4. [System Architecture](#4-System-Architecture)
|
||||
1. [Diagram](#41-Diagram)
|
||||
2. [Go Server](#42-Go-Server)
|
||||
3. [Blazor Backend](#43-Blazor-Backend)
|
||||
4. [Blazor Frontend](#44-Blazor-Frontend)
|
||||
5. [Postgresql](#45-Postgresql)
|
||||
6. [Docker](#46-Docker)
|
||||
5. [High Level Design](#5-High-Level-Design)
|
||||
1. [User Installs Module](#51-User-Installs-Module)
|
||||
2. [User Creates/Updates Role Permissions](#52-User-CreatesUpdates-Role-Permissions)
|
||||
3. [User Manages Module](#53-User-Manages-Module)
|
||||
6. [Preliminary Schedule](#6-Preliminary-Schedule)
|
||||
|
||||
## 1. Introduction
|
||||
### 1.1 Overview <!--(Mal)-->
|
||||
### 1.1 Overview
|
||||
Panoptes is a web application that allows users to manage servers and any services they control all in a single place. The system will alow users to create and manage modules, which will be used to gather data and control external services, as well as optionally install services associated with those modules. Panoptes will also allow users to create role hierarchies which will limit what functions of modules a given user can access.
|
||||
### 1.2 Business Context
|
||||
As a product, Panoptes is aimed towards any business that requires system administration, and towards Homelab administrators running their own services.
|
||||
@ -13,7 +78,7 @@ They will also particularly benefit from the permissions system, which will allo
|
||||
|
||||
Meanwhile, homelab administrators will benefit from the ability to create or install modules to monitor and control services they have set up themselves in a way that suits their niche use case.
|
||||
|
||||
### 1.3 Glossary <!--(Both)-->
|
||||
### 1.3 Glossary
|
||||
#### 1.3.1 Panoptes
|
||||
Panoptes is the name of the project - a modular web interface for managing servers and services.
|
||||
|
||||
@ -29,13 +94,13 @@ Using Panoptes you will be able to:
|
||||
- Curate a list of tools and services to monitor on the same user interface.
|
||||
- Implement user permissions to restrict or allow access to certain functions withen modules.
|
||||
|
||||
### 2.2 User Characteristics and Objectives <!--(Mal)-->
|
||||
### 2.2 User Characteristics and Objectives
|
||||
<!--(Identify the users: admin, teachers, students)
|
||||
whart are their demographics (age range) and what is their level of technical capabilities. Digital literacy.
|
||||
|
||||
What would each person like to do? What is the benefit of the software of the users-->
|
||||
The primary user of Panoptes is an administrator of a server or fleet of servers. As Panoptes is primarily aimed towards people in technical professions, it is a reasonable assumption that users will have some degree of technical knowledge.
|
||||
### 2.3 Operational Scenarios (Gaz)
|
||||
### 2.3 Operational Scenarios
|
||||
|
||||
|
||||
#### 2.3.1 Module Installation
|
||||
@ -52,19 +117,19 @@ From here they will see a summarised version of any important information regard
|
||||
|
||||
After selecting the module they will see a list of functions and configurable settings. The user selects the setting for 'port number' and changes the number. They can then save and restart the server and observe it operating on a new port.
|
||||
|
||||
#### 2.3.3 Function permission denied
|
||||
#### 2.3.3 Function Permission Denied
|
||||
|
||||
The user is a junior adminstrator in an organisation. They wish to configure a setting within a module to fix an issue however they do not have access to it as their user account has been assigned the 'junior' role within the organisation.
|
||||
|
||||
The user must ask someone holding the 'senior' role or higher to configure the setting for them as only they have access to that specific function of the module.
|
||||
|
||||
#### 2.3.4 User log in and verification
|
||||
#### 2.3.4 User Login and Verification
|
||||
|
||||
User opens Panoptes and and is prompted to either log in or create an account. To log in, the user simply will enter their username and password which will be checked against our database and authorised using the OAuth 2.0 framework.
|
||||
|
||||
Similarly, if the user has not registered an account they will be prompted to enter a username and password. Once they have done this the system will check if the username and password are valid, create the account and add it to our database.
|
||||
|
||||
### 2.4 Constraints <!--(Mal)-->
|
||||
### 2.4 Constraints
|
||||
<!--Lists general constraints placed upon the design team, including speed requirements, industry protocols, hardware platforms, and so forth.-->
|
||||
#### 2.4.1 Security Constraints
|
||||
This web application will need to be developed in a way that prevents users and malicious actors from accessing data or functions that they should not be able to access.
|
||||
@ -95,7 +160,7 @@ This is a critical feature as only authorised users should be able to access pan
|
||||
#### 3.1.3 Technical Issues
|
||||
We dont foresee any technical issues with this feature.
|
||||
|
||||
#### 3.2.4 Dependencies
|
||||
#### 3.1.4 Dependencies
|
||||
This feature is not dependant on any others.
|
||||
|
||||
### 3.2 Hierarchy Management
|
||||
@ -148,7 +213,7 @@ This feature is dependant on the ability for modules to be installed in the firs
|
||||
It also depends on our container orchestration feature so panoptes can manage the container that the module lives in.
|
||||
|
||||
|
||||
### 3.5 Container Orchestration <!--(Mal)-->
|
||||
### 3.5 Container Orchestration
|
||||
#### 3.5.1 Description
|
||||
Panoptes must be able to manage the containers used to run any modules installed on it. This will be done using the API provided by Docker.
|
||||
#### 3.5.2 Criticality
|
||||
@ -158,7 +223,7 @@ One of the biggest technical issues will be keeping track of what containers are
|
||||
#### 3.5.4 Dependencies
|
||||
This feature will not depend on any other components of the application.
|
||||
|
||||
### 3.6 Statistics Display <!--(Mal)-->
|
||||
### 3.6 Statistics Display
|
||||
#### 3.6.1 Description
|
||||
Panoptes must have a framework that can be used to display statistics. In order to achieve this, we will build a library of components that can be easily dynamically generated with statistics embedded in them.
|
||||
#### 3.6.2 Criticality
|
||||
@ -168,7 +233,7 @@ We do not foresee any technical issues with this feature.
|
||||
#### 3.6.4 Dependencies
|
||||
This feature will not depend on any other components of the application.
|
||||
|
||||
### 3.7 Security <!--(Mal)-->
|
||||
### 3.7 Security
|
||||
#### 3.7.1 Description
|
||||
As Panoptes will have a lot of access to the machine it runs on, it is important that the system is secure and cannot be used maliciously.
|
||||
#### 3.7.2 Criticality
|
||||
@ -179,7 +244,7 @@ Additionally, exposing the API that manages the containers is also a security ri
|
||||
#### 3.7.4 Dependencies
|
||||
This feature will not depend on any other components of the application.
|
||||
|
||||
## 4. System Architecture <!--(Both)-->
|
||||
## 4. System Architecture
|
||||
|
||||
<!--This section describes a high-level overview of the anticipated system architecture showing the distribution functions across (potential) system modules. Architectural components that are reused or 3rd party should be highlighted.
|
||||
|
||||
@ -187,31 +252,31 @@ list the components and write a short description.-->
|
||||
#### 4.1 Diagram
|
||||
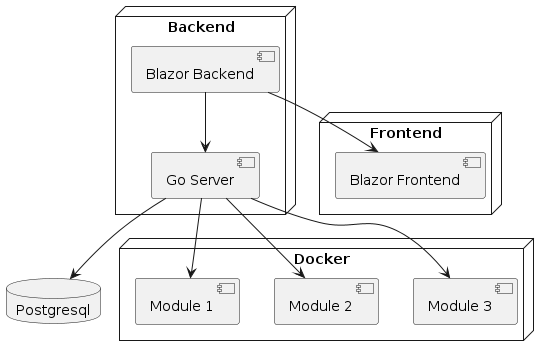
|
||||
|
||||
#### 4.1.1 Go Server
|
||||
#### 4.2 Go Server
|
||||
The Go server takes requests from the Blazor frontend, and optionally from an external service, and uses those requests to interact with the Postgresql database, with Docker, and the containers it has set up.
|
||||
#### 4.1.2 Blazor Backend
|
||||
#### 4.3 Blazor Backend
|
||||
The Blazor backend will handle all data processing between the Blazor frontend and the Go server. It will also handle any rendering that takes place for the Blazor frontend.
|
||||
#### 4.1.3 Blazor Frontend
|
||||
#### 4.4 Blazor Frontend
|
||||
The Blazor frontend will be what the user interacts with when using Panoptes. It will be used to display data, and also for the user to make any changes to to installed modules or configure the monitored services.
|
||||
#### 4.1.4 Postgresql
|
||||
#### 4.5 Postgresql
|
||||
The Postgresql database will be used to store information such as user account details and module permissions.
|
||||
#### 4.1.5 Docker
|
||||
#### 4.6 Docker
|
||||
A Docker instance will have a series of containers managed by the Go server, which will be used to store modules and be interfaced with by the Go server.
|
||||
## 5. High-Level Design <!--(Both)-->
|
||||
## 5. High-Level Design
|
||||
<!--Sequence diagrams
|
||||
state diagrams
|
||||
Data flow diagrams
|
||||
This section should set out the high-level design of the system. It should include one or more system models showing the relationship between system components and the systems and its environment. These might be object-models, DFD, etc.-->
|
||||
#### 5.1 User installs module
|
||||
#### 5.1 User Installs Module
|
||||
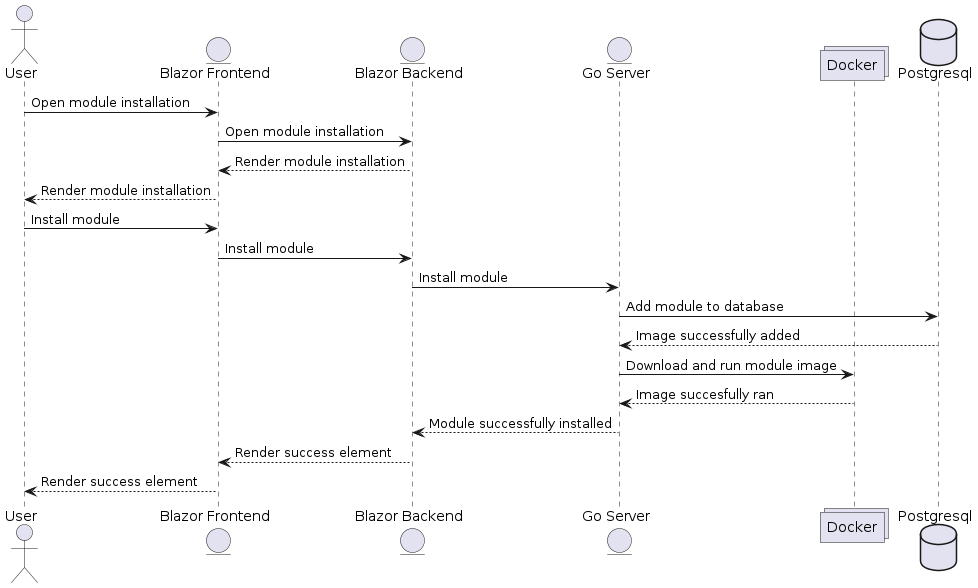
|
||||
|
||||
#### 5.2 User creates/updates role permissions
|
||||
#### 5.2 User Creates/Updates Role Permissions
|
||||
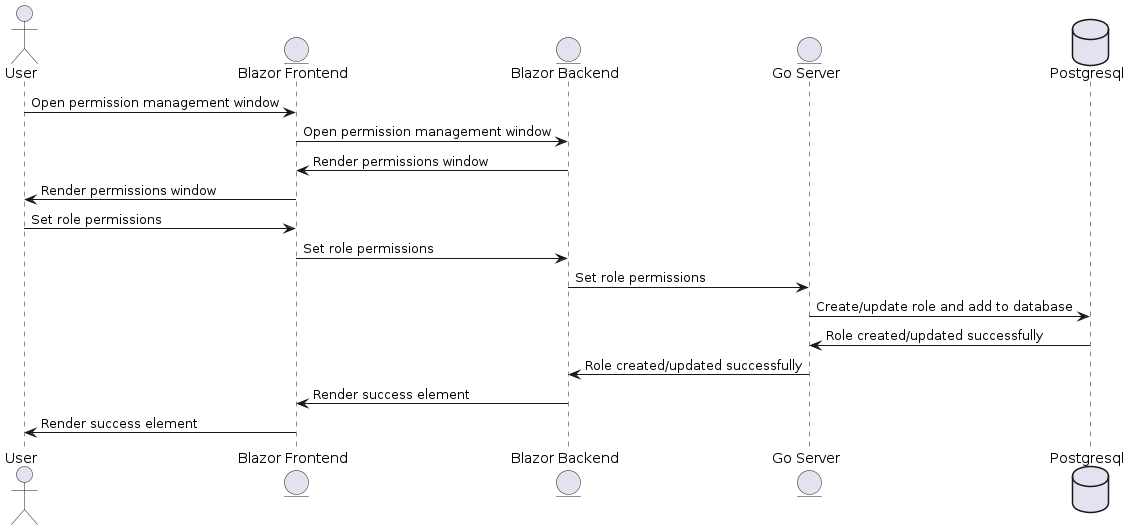
|
||||
|
||||
#### 5.3 User Manages Module
|
||||
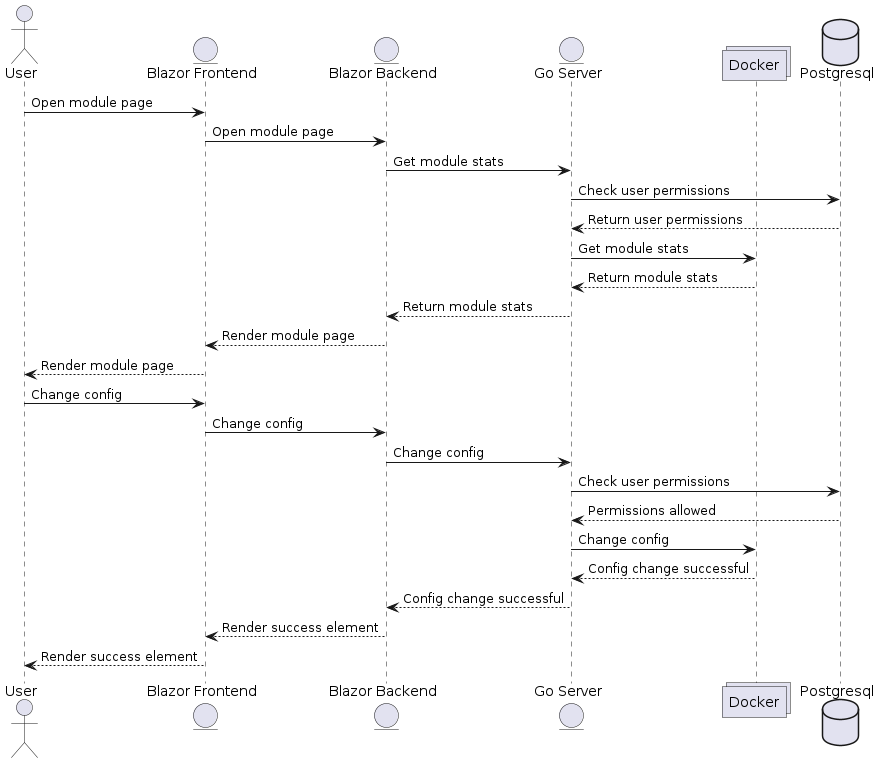
|
||||
|
||||
## 6. Preliminary Schedule <!--(Both)-->
|
||||
## 6. Preliminary Schedule
|
||||
We have set up our project into four distinct phases.
|
||||
|
||||
Phase three and four contain the bulk of the work. Phase one and two involve setting ourselves up for success by laying the foundations for phase three and four.
|
||||
@ -224,5 +289,3 @@ Phase three and four contain the bulk of the work. Phase one and two involve set
|
||||
|
||||

|
||||
|
||||
|
||||
## 7. Appendices <!--(Both)-->
|
||||
Loading…
x
Reference in New Issue
Block a user